

What is the 51% attack on bitcoin?
Will bitcoin be hijacked or something…?
Some have pointed out that "Bitcoin is at risk of a 51% attack," but considering the costs and risks involved in carrying out an attack and what an attack could do, the likelihood of a 51% attack being carried out is extremely small.
In this article, I'll explain in plain English the 51% attack on Bitcoin and the real-life examples that have happened so far with other virtual currencies.

A quick summary of this article
- A 51% attack is when a malicious miner takes control of 51% of the hash rate (computing power) to be able to perform double payments.
- The 51% attack on Bitcoin is extremely costly and has a high risk of failure, so even if it were theoretically possible, it would be extremely difficult to pull off in practice.
- A 51% attack allows double payments (sending coins sent in a previous transaction to another address again), but it does not allow falsification of past transactions, unauthorized transfer of BTC from someone else's wallet, or modification of the issuance limit.
This article was written in Japanese and converted to English using a translation tool.
Date of writing (Japanese version): February 2024
What is the 51% Bitcoin Attack?

A 51% attack is when a malicious miner takes control of 51% of the hash rate, allowing them to perform double payments.
*Miners…people who participate in mining.
*Mining…a mechanism to check transactions on the network, write them correctly in the blockchain, and get bitcoins as a reward.
*Hash rate…computing power per second of mining, mining speed.
Bitcoin doesn't have an operator, it's a new system with many computers around the world keeping a distributed network, but it also has a theoretical risk of 51% attack.


That's kind of a disturbing name, but I'd like to know how it works and what happens in a 51% attack.
How 51% Attacks Occur
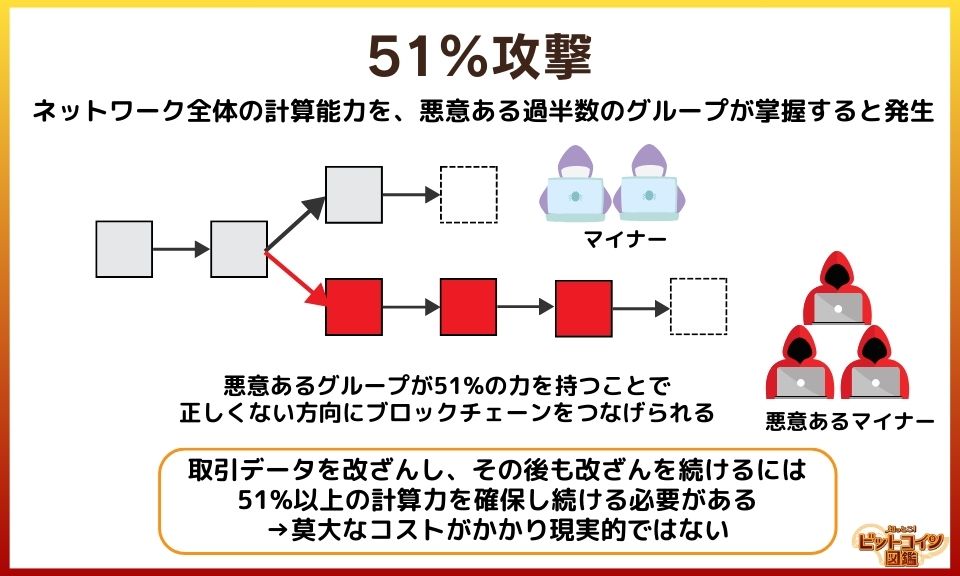
A 51% attack occurs when a majority group (or individual) controls the computing power of the entire network. When an attack occurs, the blockchain diverges, splitting into a legitimate chain and another chain.
A successful attack could theoretically control the creation of new blocks, approve transactions (transactions) for the purpose of double payment, or interfere with the confirmation of legitimate transactions.
A deeper look at how the blockchain works
- When a chain diverges, the chain with the highest cumulative DIFFICULTY is the legitimate chain.
- *Cumulative difficulty…the total amount of computational work required to generate a new block.
- When a chain splits, the miner can choose which chain to mine after in the next block mining.
- The attacker continues to mine the chain for the purpose of the attack, while the good miner continues to mine the legitimate chain.
- The attacker must continue to create chains with a higher cumulative DIFFICULTY than the legitimate chains.
- The attacker needs to maintain a hash rate of at least 51%, which is very expensive.
- If the attacker's hash rate drops and the legitimate chain has more accumulated difficulty, the attacker's fake chain will disappear.

So if a 51% attack happens, if the original legitimate chain outweighs the total amount of computational work in the attacker's chain, then the legitimate chain can be recaptured.
If the attacker's chain is invalidated, the previous blocks are also invalidated, and the attacker loses the mining reward.
Nevertheless, if a 51% attack occurs, bitcoin's credibility will drop dramatically, so a 51% attack must be prevented at all costs.

What a 51% Attack Can and Cannot Do
When a 51% attack occurs on Bitcoin, a "double payment" can be made, where the most recent transaction is sent to a different address as if it had never occurred.
However, transactions that were previously approved and incorporated cannot be pretended to have never occurred.
What the 51% attack can and cannot do
- Possible: Approval of double payments (coins sent once are sent again to another address), denial of remittance of certain transactions, monopolization of mining rewards, etc.
- Cannot: Tampering with past transactions, transferring coins from someone else's wallet without permission, changing the issuance limit, etc.
Reference:【ビットコイン研究所Q&A】マイニングの集権化、ライトニング決済とAI、Nostrのポテンシャルと課題|ビットコイナー反省会

51% attack sounds kind of scary, but it can't take away users' bitcoins or change the bitcoin issuance limit.
There is only so much you can do with a 51% attack, and the main attack is a double payment that exploits "pretending the most recent transaction never happened."

Will the 51% Problem Happen to Bitcoin?


"Bitcoin is at risk of being attacked 51% of the time!" I'm a little worried because I've seen some people say that…
Bottom line, it's very unlikely that bitcoin will be 51% attacked…

51% attack on Bitcoin is unrealistic
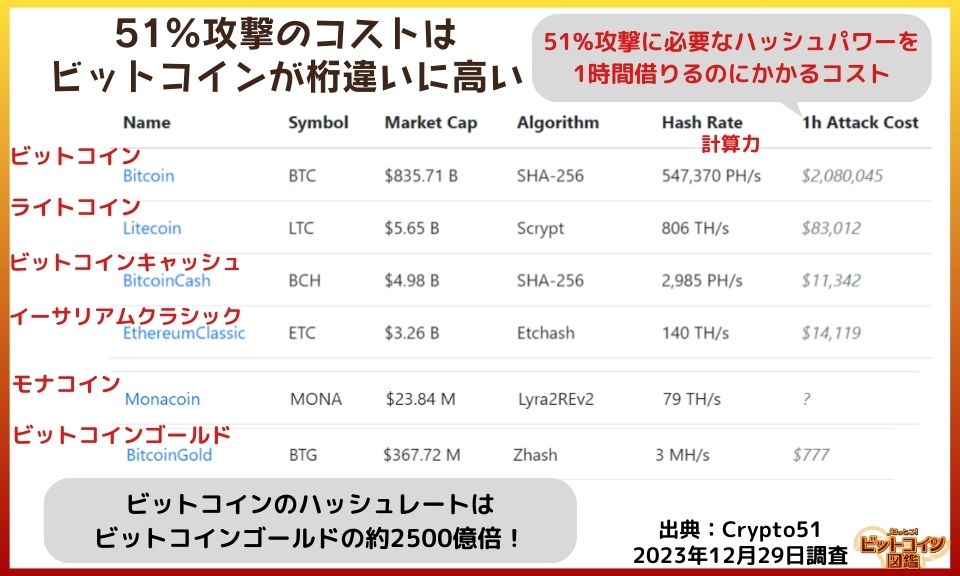
While the theoretical possibility of a 51% attack on Bitcoin exists, it is unrealistic in practice. The hash rate (computational power) of the Bitcoin network is so large that it is technically and economically difficult to run a majority hash power of the network.
Cost of a 51% Bitcoin attack
- The cost required to borrow the hash rate needed for an attack for one hour is in the hundreds of millions of yen, and when the attack stops, the network returns to normal.
- Blocks by the attacker are invalidated, so the attack must be continued incessantly.
- A large amount of mining equipment (ASIC miners, etc.) is required. Extremely difficult to assemble a huge number of high-performance machines.
- Power and operating costs.
- Huge power, cooling system, maintenance, and other operating costs are required to maintain the huge hash power.

Some experts think you need tens to hundreds of billions of dollars to carry out a 51% attack.
In a medium-sized country, that would be at the level of a year's national budget, and it doesn't seem realistic to carry out an attack that may or may not be successful.
The bitcoin community and miners are constantly monitoring the network and are expected to respond quickly to any unusual activity.

Is Collusion in Mining Pools Possible?
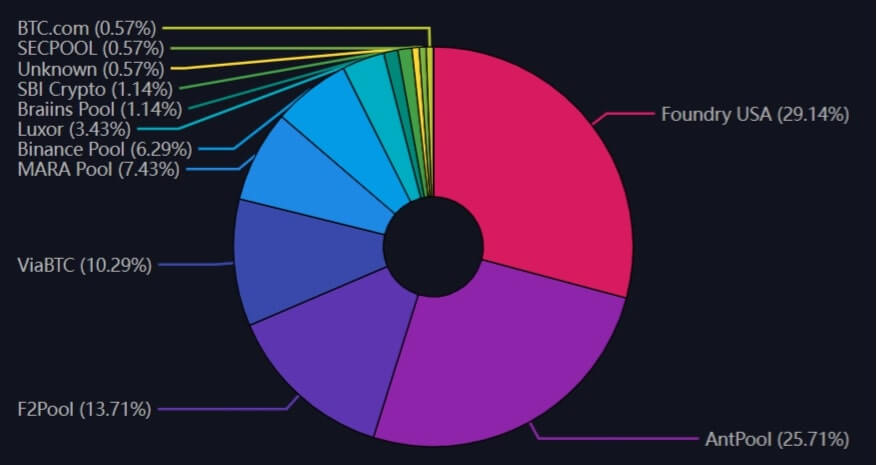
Survey, December 23, 2023
The occasional opinion that "two or three top mining pools combined can launch a 51% attack = Bitcoin is centralized" is a bit of a leap to make this claim.
*Mining pools…a system in which small-scale miners cooperate in mining and share the proceeds.
It is the miners themselves who choose the mining pool.
If a mining pool causes an attack, miners can choose to continue to be involved in the attack or switch to a mining pool that is not under attack.
It is not realistic to expect thousands or more miners to unite within a participating pool to intentionally carry out an attack.

If they did a 51% attack, the price of bitcoin held by miners would plummet, and I doubt all miners would agree to the attack….
Besides, if a mining pool plans a 51% attack, the miners who oppose the fraud will leak the information, and it's going to be hard to unite.
Mining pools that are complicit in the 51% attack will lose the trust of miners and investors.
Would a mining pool, which has a profitable long-term business model, go to the trouble of damaging its reputation? I would say "no."

It's Hard to Make Double Payments in Bitcoin
It is very difficult in practice for mining pools to collude to profit from double payments.
- Can you redeem a large amount of BTC from an exchange?
If a 51% attack is launched and profit is targeted, it would have to be a very large amount to make the original payment.
Large transactions may alarm exchanges, and the attack may fail due to lack of quick withdrawals. - Can the executor be trusted?
If executor A converts a huge amount of bitcoins into legal tender, and then conducts a 51% attack, executor A will get both the original bitcoins & the converted currency.
But we don't know if the funds obtained by executor A will be distributed to the cooperating parties in the mining pool, and we need to trust that "executor A will not abscond with the money."
When 51% attacks have occurred in the past on other virtual currencies, some exchanges have responded by increasing the number of block approvals (lengthening the time it takes for a transaction to be considered complete). The more vigilant an exchange is, the more likely it is that a 51% attack will fail.


It would certainly be suspicious if an address that sent a huge amount of BTC to an exchange immediately tried to convert it to legal tender for withdrawal.
It's also going to be difficult for the exchanges to immediately respond to the huge amount of money in the first place.
51% Attack to Monopolize Block Rewards is Inefficient
Conducting a 51% attack in order to monopolize block rewards from mining is extremely inefficient in terms of cost and risk. Even if the attacker were to monopolize the block reward, the cost of a 51% attack is enormous, even more than the reward.
In addition, if the original chain has more total computational work than the attacker's chain, the attacker's chain will be invalidated and the block reward will be invalidated as well. There is a risk that all of the enormous computational resources invested will be wasted.

There was an opinion that pointed out that "51% could be done to monopolize the mining rewards," but that would actually require a ton of money and computing power, and that's just not realistic.
If you have enough computing resources to do a 51% attack, it's much more efficient to do normal mining without any attacks.

51% Attack & BTC Short Uncertainty
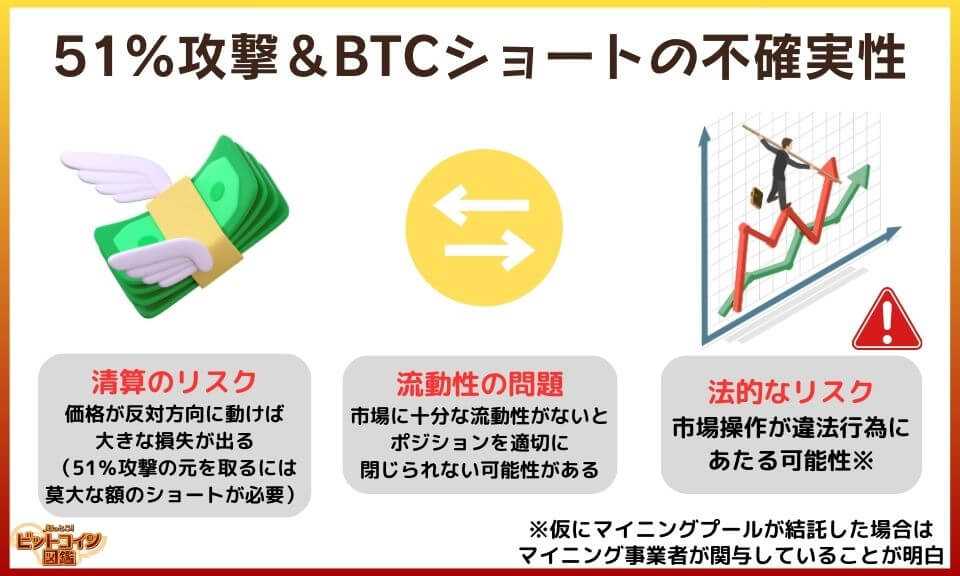
The strategy of "making a 51% attack on Bitcoin while simultaneously setting up a short position (a trade betting on a decline)" is conceivable in theory but impractical in practice.
- Liquidation Risk
A significant amount of shorting is required to make up for the 51% attack. - Liquidity problem
When taking a large short position, if there is not enough liquidity in the market, it may not be possible to buy back the position at the right price when closing it (fixing the profit). - Legal Risks
Market manipulation by 51% attack may be illegal (if mining pools collude, it is obvious that mining operators are involved).
There is no precedent for legal risk, and I don't know what will happen, but market manipulation is certainly considered illegal in many countries.
The operators involved in the attacks could be held criminally liable, or they could be sued in civil court.


In the Terra (LUNA) and UST crash of 2022, it looks like the former CEO of FTX is being investigated for alleged price manipulation.
Even if they crashed the market and profited from shorting, the chain collapse of virtual currency related companies/projects may come back to haunt the attackers in a roundabout way…
Actual Example of 51% Attack on PoW Blockchain


I'd like to know a real-life example of a 51% attack on a virtual currency.
I'll show you the Monacoin Ethereum Classic Bitcoin Gold case as an actual example of a 51% attack.

51% Attack on Monacoin
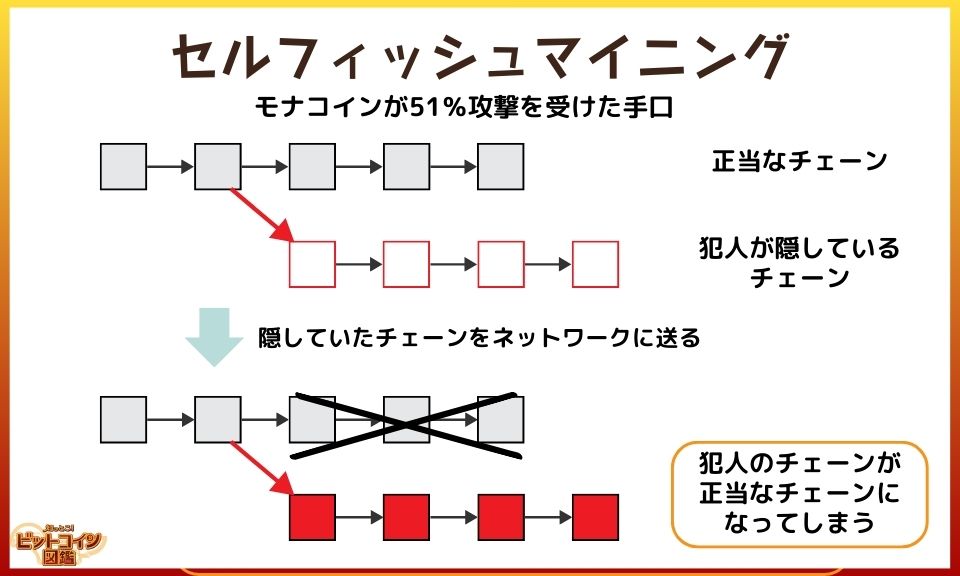
In 2018, Monacoin, which originated in Japan, suffered a 51% attack, resulting in the unauthorized withdrawal of Monacoin worth approximately 10 million yen at the then rate. In contrast to Bitcoin, which has a huge hash rate (computational speed) required for the attack, Monacoin is attacked with an order of magnitude less hash power.
51% attack on Monacoin
- Selfish Mining: After the culprit successfully mines, the block is hidden without telling the network, and the hidden chain is stretched. When the chain becomes longer than the public chain, it is sent to the network and the culprit's chain is adopted by the public chain.
- The Culprit's M.O.: The culprit deposits Monacoin on the exchange in advance and redeems it. Afterwards, the hidden chain was released to the network, and the attacker pretended that the Monacoin that should have been deposited and redeemed at the exchange was not transferred. (The attacker is left with both the Monacoin he should have transferred and the money he withdrew from the exchange.)
- Finality: In most cases, settlement is considered complete only after 3-6 blocks (approximately 30-60 minutes) for Bitcoin and 18-24 blocks (approximately 27-36 minutes) for Monacoin have been approved. Each virtual currency exchange sets its own number of approvals for each brand, but the affected exchanges were targeted because they had a low number of approvals.

So Monacoin, with its short approval interval and low hash rate, was targeted…
As a measure to prevent the 51% attack on Monacoin, exchanges are implementing measures to increase the number of block approvals.
In 2018, there was no ASIC (hardware made for a specific purpose) specifically for Monacoin, but now that there is an ASIC, the hash rate has increased dozens of times.

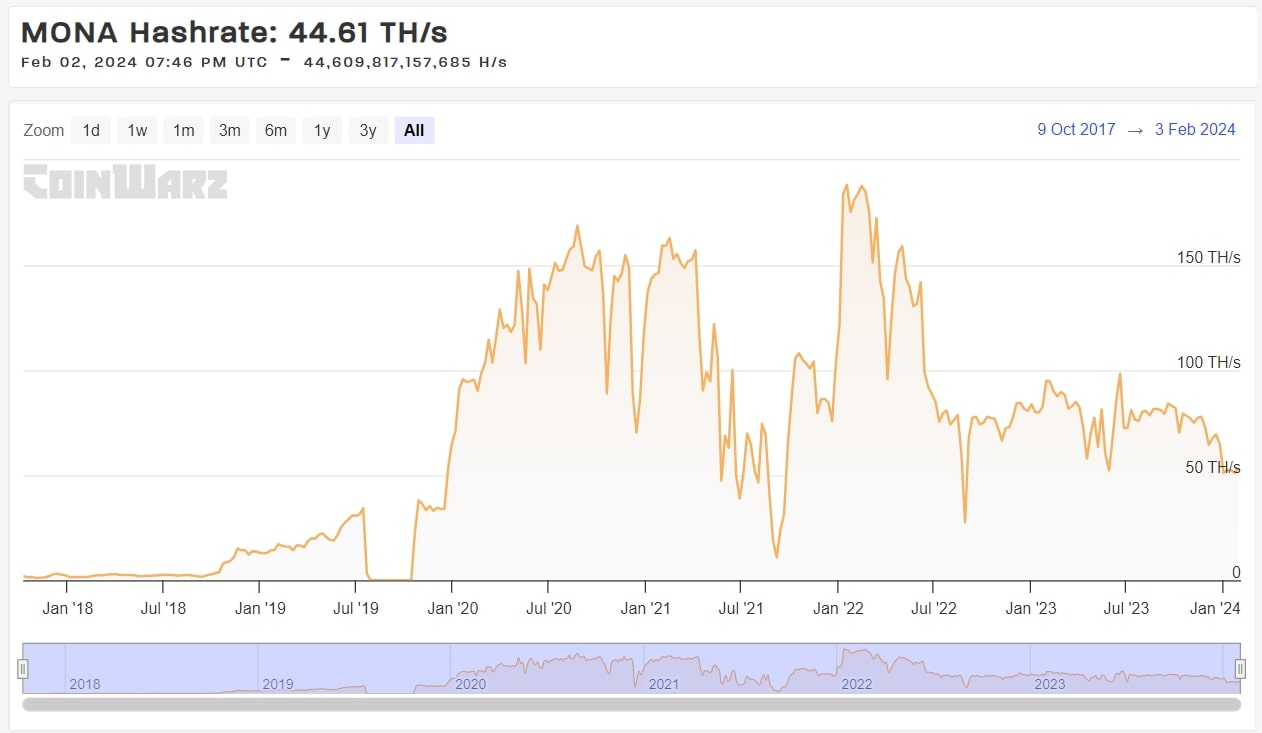
Feb 3, 2018: 1.5 TH/s Feb 3, 2024: 64.6 TH/s

That's more than a 40-fold increase in hashrate in six years!
You can see the attack difficulty has increased dramatically compared to what it was in 2018.
Each of the PoW virtual currencies is working on 51% attack protection.
Do your own research on the virtual currency you are interested in.

51% Attack on Ethereum Classic
In 2020, Ethereum Classic (ETC), a hard fork (branch) of Ethereum in the past, suffered a 51% attack. It was attacked three times in August, with the first attack resulting in double payments worth approximately $5.8 million (about $600 million at the then rate).
Hackers purchased the hashrate to carry out the attacks, and the cost of the 51% attack is estimated to have been about $190,000.
The hackers mined over 3,000 blocks offline, then released them to the network and split the chain.


You deposited ETCs from a chain that was not 51% attacked to an exchange, sold ETCs on the exchange, and then published the chain you mined to make a double payment.
51% Attack on Bitcoin Gold
In 2020, Bitcoin Gold (BTG), which was created in a hard fork of Bitcoin, suffered a 51% attack. The double payments caused damage worth approximately 2 billion yen at the rate of the time.
Twenty-two blocks were manipulated, and the developers of Bitcoin Gold asked the exchange to stretch the approval number by 50 blocks.
As of December 2023, the hash rate (computing power) is 506,264 PH/s (peta hash/s) for bitcoin and 2 MH/s (mega hash/s) for bitcoin gold.


Bitcoin and Bitcoin Gold have hash rates that are about 250 billion times different!
I thought that Bitcoin Gold might be more difficult to attack because of the name "Bitcoin", but I was surprised to see the difference in hash rate.
Is there a 51% problem with the PoS blockchain?


We know there is a 51% problem with PoW, but what about other virtual currencies besides PoW?
Although different in nature, the 51% problem (33% problem) is also mentioned in PoS, which is mainstream in altcoins.

PoS (Proof of Stake)
- Participation in the blockchain network by holding the relevant coins rewards newly issued coins. Staking allows you to participate in the governance voting of the network (decision-making process for project direction, updates, rule changes, etc.)
- Concentration of Wealth
In PoS, the more coins you hold, the easier it is to earn yield coins, and there is a risk of wealth concentration among large holders of coins. In governance voting, votes may be cast in favor of large holders (often held by large investors and operators of initial holders, virtual currency exchanges that manage large amounts of user funds, etc.) - Theoretically possible to attack, but difficult in practice
There is little advantage to attacking in the PoS network because it is necessary to hold the relevant coins in order to attack, and the attacker's attack would reduce the value of the tokens
Voting whales (large holders of tokens) have a large impact on governance voting
- Solend crisis
→ Governance vote to grant emergency authority to Solend Labs for the liquidation crisis of a single user who owed $107 million on Solana's DeFi (Solend Labs tried to prevent the worst from happening by properly liquidating the position on behalf of a single user who could not be contacted). The governance vote passed with Vote Whale voting in favor (note that the lone user was later contacted, so the liquidation never took place and the crisis was resolved). - Uniswap
→ When the vote was taken to deploy Uniswap V3 on the BNB chain, a16z, a venture capital firm with large holdings in UNI, voted against it by 15 million votes (the total number of votes cast was about 83 million, resulting in 66% of the votes in favor of passage). The opposition by a16z is believed to be due to the fact that a16z's investment, "Layer Zero," was not adopted by the Bridge. - Mango
→ Hackers stole DeFi token "MNGO" and used stolen tokens to manipulate governance voting.

So the governance vote is more likely to go to those who hold large amounts of tokens.
Bitcoin in PoW feels a bit different in nature, since you can't influence the blockchain network by holding a lot of coins
As for attacks on PoS networks, I think each project has its own countermeasures, so if you are interested, check them out individually.
Here are some articles describing 51% attack (33% attack).

- イーサリアムのプルーフ・オブ・ステークにおける攻撃および防御|Ethereum.org (updated 2023)
- 各通貨には何%攻撃ができるのか?(BTC, ETH, XRP, EOS)|Leona Hioki (日置 玲於奈 )|Medium (Writing date: 2019)
How to prevent 51% attacks.


Is there a way to counter 51% attacks…?
I'll show you some countermeasures to prevent 51% attacks.

Exchanges increase the number of block approvals
When an exchange "increases the number of block approvals," it means that it performs more checks to ensure that the transaction is indeed correct. For example, where they originally performed 5 block checks, they now perform 10 block checks.
Since it is difficult for an attacker to continue an operation for double payment for a long period of time, an increase in the number of block approvals makes it easier to spot unnatural transactions and detect malicious transactions before they take place on the exchange.
When Monacoin was attacked 51% of the time, some domestic exchanges raised the number of approvals from around 24 blocks to 100 blocks.


So if the exchanges were aware of the anomaly, they might be able to limit the spread of damage caused by the 51% attack.
Decentralization of Mining Pools
Various forms of mining pools are being devised to prevent the concentration of mining pools.
Mining Pool Decentralization Initiatives
- StratumV2
→ Mining protocol. Miners have the authority to select transactions to be included in a block, decentralizing mining and increasing Bitcoin's resistance to censorship. - OCEAN
→ Mining decentralization project, distributing block rewards directly to miners. Jack Dorsey participated in investment.

The current mining pools also allow participating miners to move freely from one pool to another, but many people say it's not good to have the power biased toward a few pools.
Many bitcoiners are looking forward to the implementation of StratumV2 to increase mining security and censorship resistance.

[summary] What is the 51% Attack on Bitcoin?

Key Points
- A 51% attack is when a malicious miner takes control of 51% of the hash rate, allowing them to perform double payments.
- The 51% attack on Bitcoin is extremely costly and has a high risk of failure, so even if it were theoretically possible, it would be extremely difficult in practice.
- Projects are also underway to prevent centralization of mining pools.

I thought the 51% attack was "all the bitcoins get hijacked!" I thought it was something like that, but you can't take people's bitcoins or change the bitcoin issuance limit.
In the past, 51% attacks have occurred on Monacoin and Ethereum Classic, but the hash rate (computing power) required to attack Bitcoin is orders of magnitude greater, so a 51% attack on Bitcoin is considered unrealistic.


I was kind of nervous about bitcoin because it seems difficult and I don't really understand how it works, but now I want to know a lot more about it.
I want to know more about Bitcoin!
Recommended Articles:What is Bitcoin?

Writer:Sigeru Minami
Creator of "Bitcoin-zukan.com."
Active as a handmade craftsman of Bitcoin goods.
